It's been a long time, so I will probably get some of this wrong, but my understanding used to be that "root" is like the delivered administrator account on a server or computer running Linux or Unix OS. The password for root should be changed by the administrator of the system upon initial install and new pw should only be shared with very restricted / trusted admins only. Otherwise it's extremely vulnerable to hacking. Further, if they don't know or won't supply the new password for root, then the auditors can't act as admins and really dig into the system directories and files. It sounds like the county provided some username/pw to Cyber Ninjas, but not the root pw.outofstateaggie said:will25u said:.@BennettArizona told me that #AZAudit is missing root passwords for precinct scanners. @maricopacounty by letter informed that that they have given them all passwords and do not have what they are looking for. pic.twitter.com/LLdhuTubkJ
— The AZ - abc15 - Data Guru (@Garrett_Archer) May 6, 2021
Are the passwords they are talking about original with the equipment? Like a generic password that would need to be changed by the county once they take possession/purchase the equipment? I'm lost.
*****OFFICIAL ELECTION DAY THREAD*****
2,700,198 Views |
20889 Replies |
Last: 2 yr ago by Whistle Pig
Good info. Thank you.
Assuming you are correct, then it becomes a tracing of the chain of custody by precinct question. The precinct election official receiving the machines would need the root password for the install of the software for that particular election location, correct?Quote:
It's been a long time, so I will probably get some of this wrong, but my understanding used to be that "root" is like the delivered administrator account on a server or computer running Linux or Unix OS. The password for root should be changed by the administrator of the system upon initial install and new pw should only be shared with very restricted / trusted admins only. Otherwise it's extremely vulnerable to hacking. Further, if they don't know or won't supply the new password for root, then the auditors can't act as admins and really dig into the system directories and files.
I wonder if a consultant or Dominon employee set up all the machines with the same root pw and the county is going to say they don't know it. CyberNinjas needs to be root to access all directories on they system. Otherwise, their audit scope will be severely limited.aggiehawg said:Assuming you are correct, then it becomes a tracing of the chain of custody by precinct question. The precinct election official receiving the machines would need the root password for the install of the software for that particular election location, correct?Quote:
It's been a long time, so I will probably get some of this wrong, but my understanding used to be that "root" is like the delivered administrator account on a server or computer running Linux or Unix OS. The password for root should be changed by the administrator of the system upon initial install and new pw should only be shared with very restricted / trusted admins only. Otherwise it's extremely vulnerable to hacking. Further, if they don't know or won't supply the new password for root, then the auditors can't act as admins and really dig into the system directories and files.
A hard drive uses mechanical platters with a read/write head to access the data on the platters. Hard drives are older tech, but more vulnerable to shock and physical damage.Quote:
What's the difference?
A solid state drive has no moving parts and uses memory chips to store the state. Pretty much the same thing as USB thumb drives. Dropping a SSD is far less likely to do any damage to it, while dropping a hard drive can kill it.
"If you will not fight for right when you can easily win without blood shed; if you will not fight when your victory is sure and not too costly; you may come to the moment when you will have to fight with all the odds against you and only a precarious chance of survival. There may even be a worse case. You may have to fight when there is no hope of victory, because it is better to perish than to live as slaves." - Sir Winston Churchill
Got it! Thanks, again.
Meanwhile in Wisconsin, Kenosha is now getting into the law suit game. Green Bay and Racine have already filed their own suits.
Quote:
Six Kenosha residents have filed a complaint with the Wisconsin Elections Commission alleging the city allowed liberal outside groups to take over running November's election.
The action is the latest in a growing number of election law complaints against the "famous WI-5"the cities of Milwaukee, Madison, Green Bay, Kenosha, and Racine.
But unlike in Green Bay, where the city's clerk challenged the infiltration by the outside groups and meddling city officials, emails obtained by Wisconsin Spotlight show that election officials in the other four Democratic Party strongholds were glad to go along for the well-funded ride.
The emails show how deeply entrenched the Chicago-based Center for Tech and Civic Life's network of left-wing "partners" was in administering elections in the five Wisconsin citiesand how partisan the activists were.
Quote:
The six residents filed the complaint against Kenosha Mayor John Antaramian, City Clerk Matt Krauter, and Wisconsin Elections Commission Administrator Meagan Wolfe.
They allege that the city violated the U.S. Constitution's elections and electors clauses by signing contracts with third-party groups that allowed those groups to take over large facets of election administration.
Residents of Green Bay and Racine have filed similar complaints.
"You are the famous WI-5. Congrats on successful administration of last week's state primary!" Whitney May, Center for Tech and Civic Life's director of government services, wrote to local election officials in the five cities after the statewide primary elections in August. "Excited to see November be an even bigger success for you and your teams."
With November in mind, May wanted to connect the election officials to a CTCL partner, the Center for Civic Design, which is a Maryland-based policy organization focused on election administration that partners with left-of-center organizations such as Pierre Omidyar's Democracy Fund. Omidyar is founder of the multinational e-commerce corporation eBay and a generous donor to Democratic causes and candidates.
Center for Civic Design likes to say that "democracy is a design problem."
"The center focuses efforts on the nearly 30 million voters that are not fully fluent in English. It seeks to shape the voting experience and voting materials to ease voter comprehension and increase their voter participation," InfluenceWatch notes.
LinkQuote:
Nelson did not return a call seeking comment, nor did Krauter, the city clerk-treasurer. Antaramian, the mayor, did not respond to requests for comment Monday.
In a one-sentence email Wednesday morning to Wisconsin Spotlight, Kenosha City Administrator John W. Morrissey said: "We believe the complaint filed with the Wisconsin Elections Commission is frivolous."
Asked to explain why, Morrissey replied in a second email: "No, we will let it follow the process."
The emails show that Kenosha, like the four other "WI-5" cities, signed a contract with the Center for Tech and Civic Life for the $862,779 in grant money that the city received.
That's the real rub, legally speaking, say the lawyers representing the complainants in Kenosha, Green Bay, and Racine. Binding city election officials to the terms of an outside groups' "election safety and security" contract, they say, is at odds with the U.S. Constitution. That document designates municipal clerks and the Wisconsin Elections Commission as the only overseers of elections in the state.
So, what is our current status?
Issues have been found? Have not? I'm seeing a ton of back and forth random ****, but nothing about details. Is that intentional?
Issues have been found? Have not? I'm seeing a ton of back and forth random ****, but nothing about details. Is that intentional?
Part of the agreement is that only the final report will be released to the state senate. No piecemeal reports.Stupid@17 said:
So, what is our current status?
Issues have been found? Have not? I'm seeing a ton of back and forth random ****, but nothing about details. Is that intentional?
Albatross Necklace said:
Unconfirmed rumor:
During the Michigan audit some of Microsoft's custom firmware was found in a voting machine.
Quote:
DePerno said forensic images obtained in December 2020 show machines were connected to the internet, and evidence of "even remnants of foreign connections."
"We're the only case in the country that's been actually able to look at forensic images," he told War Room, Wednesday. "Dec. 6, 2020 we went into Antrim County and collected forensic images of [Dominion's] election management system. We've been studying them since that time."
Quote:
DePerno and his team say they have "proof that voting machines used in the 2020 elections can be compromised and votes easily transferred from one candidate to another."
DePerno said they uncovered a Microsoft "implant" installed on the machines that was not authorized by the election commission, "which means the actual system itself would be decertified."
"You can use this type of program go directly in the database and circumvent any of these terrible easy security features Dominion has and manipulate any system they have," he said.
LinkQuote:
Dominion wants to create this narrative which is a false narrative that their system is secured," he said.
DePerno questioned the company's legitimacy, when their machines could be so easily compromised.
"If you are a legitimate software companythat would be used in a national election there is no way that you would ever program a system that works like this," he said.
DePerno said "it's a complete lie" that his case in Michigan has no traction, or evidence.
"We have plenty of traction in this case, the evidence we have is actual evidence, it's been verified over and over again," he said.
"We put it into the court record," Deperno said. "It's right there for everyone to see."
The router might have saved info like open ports, routing info, allowed IP address, assignment IP address pools, etc. It's all about allowing devices to connect through the router to another network (Like the Internet). A router just "routes" data packets from one network to another.aggiehawg said:So then all of the claims about law enforcement and people's SS# is complete crap, then?FriscoKid said:Correctaggiehawg said:Routers aren't exactly storage devices, are they? They would show which IP addresses were connected but not the information that was exchanged?will25u said:
Routers would show what Vlan(network), ip address, mac address(physical hardware address, unique to each network card).
There are also logs of what mac address connected to which port at what time. Etc.
It would be very useful to find out if a device had access to the internet or not.
I don't know why law enforcement information would be on it, except if the router was used at a police precinct, or if LEO connected to the router/switch or wifi if the wifi access point was connected to the router.
ETA: routers hold a lot of information as they are the gatekeepers to the network(s).
No, it wouldn't store stuff like Social Security Numbers.
Hillary paid for warrant to spy on Trump.
We'll go one better. If Maricopa County never had admin access, they allowed Dominion to run their election, not the county election officials. Whereas Dominion's CEO, Poulos had testified repeatedly that they did not "run the elections" for any state nor state subdivision. Both of those things cannot be true at the same time.oh no said:I wonder if a consultant or Dominon employee set up all the machines with the same root pw and the county is going to say they don't know it. CyberNinjas needs to be root to access all directories on they system. Otherwise, their audit scope will be severely limited.aggiehawg said:Assuming you are correct, then it becomes a tracing of the chain of custody by precinct question. The precinct election official receiving the machines would need the root password for the install of the software for that particular election location, correct?Quote:
It's been a long time, so I will probably get some of this wrong, but my understanding used to be that "root" is like the delivered administrator account on a server or computer running Linux or Unix OS. The password for root should be changed by the administrator of the system upon initial install and new pw should only be shared with very restricted / trusted admins only. Otherwise it's extremely vulnerable to hacking. Further, if they don't know or won't supply the new password for root, then the auditors can't act as admins and really dig into the system directories and files.
Quote:
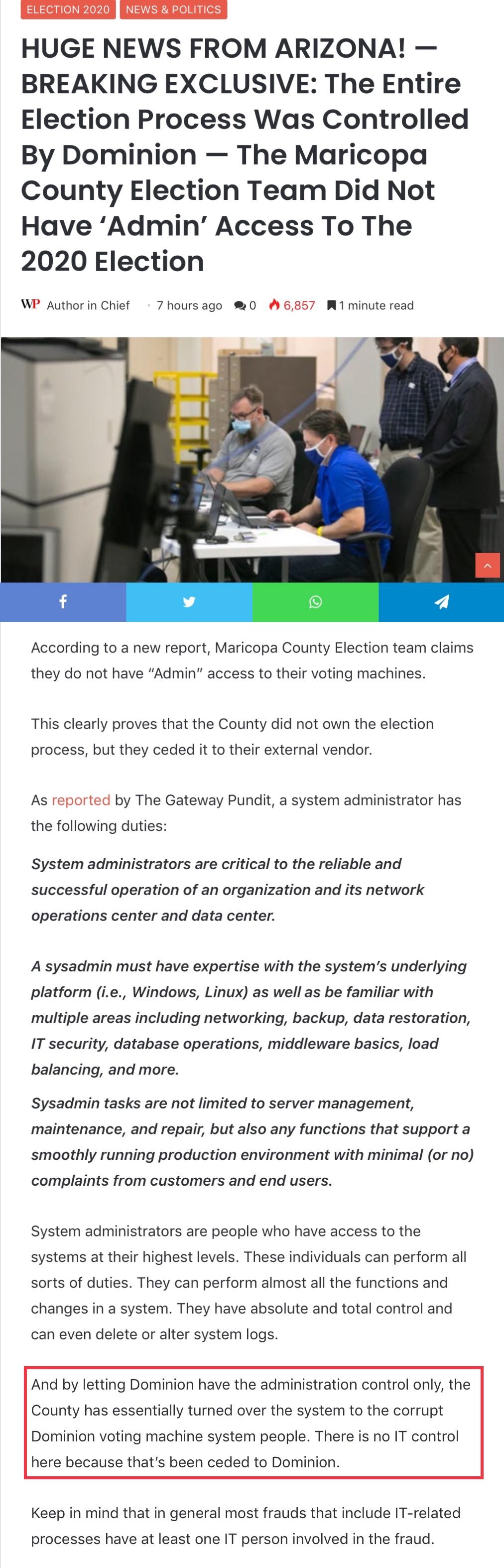
It would likely be impossible to run an election without these. The Maricopa County Election team claims they do not have 'Admin' access to their voting machines. If this is the case, then the County did not own the election process they ceded it to their external vendor.
Quote:System administrators are individuals who have access to the systems at their highest levels. These individuals are able to perform all sorts of duties. They are able to perform most all the functions and changes in a system. They have complete and total control and can even delete or alter system logs.Quote:
System administrators are critical to the reliable and successful operation of an organization and its network operations center and data center. A sysadmin must have expertise with the system's underlying platform (i.e., Windows, Linux) as well as be familiar with multiple areas including networking, backup, data restoration, IT security, database operations, middleware basics, load balancing, and more. Sysadmin tasks are not limited to server management, maintenance, and repair, but also any functions that support a smoothly running production environment with minimal (or no) complaints from customers and end users.
Video at LinkQuote:
The fact that the County does not have system administrators who have administrative access to the Dominion voting machines is a big concern. By allowing Dominion to have the administration access only, the County has basically turned over the system to the Dominion voting machine system people. There is no IT control here because that's been ceded to Dominion.
If I am Dominion and Maricopa County is lying. start squealing like a stuck pig. Because if Maricopa County is telling the truth, Dominion is screwed.
Very predictable.will25u said:Source at the county says DOJ is going to get involved in some capacity with the #azaudit. #azauditpool
— The AZ - abc15 - Data Guru (@Garrett_Archer) May 6, 2021
If DOJ orders federal law enforcement to intervene it would be interesting if state law enforcement arrested them on the spot and placed them in jail.
Constitutional crisis
Among the latter, under pretence of governing they have divided their nations into two classes, wolves and sheep.”
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
If true people need to go to jail.aggiehawg said:Albatross Necklace said:
Unconfirmed rumor:
During the Michigan audit some of Microsoft's custom firmware was found in a voting machine.Quote:
.......
Among the latter, under pretence of governing they have divided their nations into two classes, wolves and sheep.”
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
So let's go back to this picture.

If nightly totals are being taken off the machines and being removed to another location. How does that square with the lack of admin codes??

If nightly totals are being taken off the machines and being removed to another location. How does that square with the lack of admin codes??
WTF does the DOJ have any say in this. Seems like a conflict of interests under the circumstancesrichardag said:Very predictable.will25u said:Source at the county says DOJ is going to get involved in some capacity with the #azaudit. #azauditpool
— The AZ - abc15 - Data Guru (@Garrett_Archer) May 6, 2021
If DOJ orders federal law enforcement to intervene it would be interesting if state law enforcement arrested them on the spot and placed them in jail.
Constitutional crisis
'Justice' Department - you need to stay in your lane. Do not touch Arizona ballots or machines unless you want to spend time in an Arizona prison.https://t.co/W7l3WhFsjt
— Wendy Rogers (@WendyRogersAZ) May 6, 2021
Hillary paid for warrant to spy on Trump.
Kind of a catch 22 for Marcopa Count election officials.aggiehawg said:oh no said:aggiehawg said:Quote:
....Quote:
It would likely be impossible to run an election without these. The Maricopa County Election team claims they do not have 'Admin' access to their voting machines. If this is the case, then the County did not own the election process they ceded it to their external vendor.Quote:System administrators are individuals who have access to the systems at their highest levels. These individuals are able to perform all sorts of duties. They are able to perform most all the functions and changes in a system. They have complete and total control and can even delete or alter system logs.Quote:
.....Video at LinkQuote:
The fact that the County does not have system administrators who have administrative access to the Dominion voting machines is a big concern. By allowing Dominion to have the administration access only, the County has basically turned over the system to the Dominion voting machine system people. There is no IT control here because that's been ceded to Dominion.
If I am Dominion and Maricopa County is lying. start squealing like a stuck pig. Because if Maricopa County is telling the truth, Dominion is screwed.
Among the latter, under pretence of governing they have divided their nations into two classes, wolves and sheep.”
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
The Feds meddling in states rights. The Arizona legislators have voted the courts have spoken, but the leftists progressives bureaucrats at the federal level are outraged.captkirk said:WTF does the DOJ have any say in this. Seems like a conflict of interests under the circumstancesrichardag said:Very predictable.will25u said:Source at the county says DOJ is going to get involved in some capacity with the #azaudit. #azauditpool
— The AZ - abc15 - Data Guru (@Garrett_Archer) May 6, 2021
If DOJ orders federal law enforcement to intervene it would be interesting if state law enforcement arrested them on the spot and placed them in jail.
Constitutional crisis
Among the latter, under pretence of governing they have divided their nations into two classes, wolves and sheep.”
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Exactly. They can't have it both ways.richardag said:Kind of a catch 22 for Marcopa Count election officials.aggiehawg said:oh no said:aggiehawg said:Quote:
....Quote:
It would likely be impossible to run an election without these. The Maricopa County Election team claims they do not have 'Admin' access to their voting machines. If this is the case, then the County did not own the election process they ceded it to their external vendor.Quote:System administrators are individuals who have access to the systems at their highest levels. These individuals are able to perform all sorts of duties. They are able to perform most all the functions and changes in a system. They have complete and total control and can even delete or alter system logs.Quote:
.....Video at LinkQuote:
The fact that the County does not have system administrators who have administrative access to the Dominion voting machines is a big concern. By allowing Dominion to have the administration access only, the County has basically turned over the system to the Dominion voting machine system people. There is no IT control here because that's been ceded to Dominion.
If I am Dominion and Maricopa County is lying. start squealing like a stuck pig. Because if Maricopa County is telling the truth, Dominion is screwed.
If the audit is able to turn up fraud, I would expect the County to start throwing Dominion under the bus in a heartbeat! Got to protect those government pensions.
"ROGER - OUT"
The administrator may grant user access to certain files, usually through a user password (or no password and any one can download) Completely up to the discretion of the administrator whoever that may be.aggiehawg said:
So let's go back to this picture.
If nightly totals are being taken off the machines and being removed to another location. How does that square with the lack of admin codes??
Among the latter, under pretence of governing they have divided their nations into two classes, wolves and sheep.”
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
Thomas Jefferson, Letter to Edward Carrington, January 16, 1787
The second part of the rumor was speculation that the Gates divorce was less about marital strife than shielding assets & limiting liabilities.richardag said:If true people need to go to jail.aggiehawg said:Albatross Necklace said:
Unconfirmed rumor:
During the Michigan audit some of Microsoft's custom firmware was found in a voting machine.Quote:
.......
To expand a bit on the "root" vs "admin" conversation.
It is standard practice for "hardening" a system (making it more secure) to disable the "root" user on a UNIX/LINUX based system. You can create accounts with access to "sudo" or "Super User DO". This is done for a number of reasons.
1) Having root enabled gives a hacker one of two pieces of info to start with (user and password). It is also the known account name for the master super user account
2) You cannot track "who did what" when people login with "root" and execute commands. They get jumbled with system process and everything else on the server
At a minimum, if I were setting up the system, I would disable root access to the server from SSH. Meaning, no remote admin access to the server. Personally I would even disable root access all together, but at least limit it to someone with physical access to the server.
Next, everyone should have their own account to track who does what. And password policies should be implemented to ensure they are strong enough to fight hacking.
Then I would implement multi-factor authentication. So you would have to have your username, a strong password, and something like your phone or key fob with a PIN that would be required to confirm you are who you are.
Data on the drives would be encrypted (I guess this is really a DUH!)
Finally, each account would be limited to access to only those applications or tasks they were allowed. UNIX based operating systems are awesome for granular permissions. You can set every single item on the server to Read, Read/Write, and Execute permissions based on User and/or Group.
You can be damn sure I would never allow the "write" permission on any of the data files by a user, only by an application user.
I know this is a TLDR down nerd-lane, but to me, this is sh*t a system admin with 2-5 year experience should know and be fired for not doing so.....
It is standard practice for "hardening" a system (making it more secure) to disable the "root" user on a UNIX/LINUX based system. You can create accounts with access to "sudo" or "Super User DO". This is done for a number of reasons.
1) Having root enabled gives a hacker one of two pieces of info to start with (user and password). It is also the known account name for the master super user account
2) You cannot track "who did what" when people login with "root" and execute commands. They get jumbled with system process and everything else on the server
At a minimum, if I were setting up the system, I would disable root access to the server from SSH. Meaning, no remote admin access to the server. Personally I would even disable root access all together, but at least limit it to someone with physical access to the server.
Next, everyone should have their own account to track who does what. And password policies should be implemented to ensure they are strong enough to fight hacking.
Then I would implement multi-factor authentication. So you would have to have your username, a strong password, and something like your phone or key fob with a PIN that would be required to confirm you are who you are.
Data on the drives would be encrypted (I guess this is really a DUH!)
Finally, each account would be limited to access to only those applications or tasks they were allowed. UNIX based operating systems are awesome for granular permissions. You can set every single item on the server to Read, Read/Write, and Execute permissions based on User and/or Group.
You can be damn sure I would never allow the "write" permission on any of the data files by a user, only by an application user.
I know this is a TLDR down nerd-lane, but to me, this is sh*t a system admin with 2-5 year experience should know and be fired for not doing so.....
Thanks! Appreciate the insight and info.
One reason the devices may have been removed to another location is it was part of the site's disaster recovery plan. It's a pretty standard practice to store backups off-site. Not saying this is what happened in Maricopa County. It's unclear why the devices were relocated nightly.aggiehawg said:
So let's go back to this picture.
If nightly totals are being taken off the machines and being removed to another location. How does that square with the lack of admin codes??
Very small contribution compared to the information you and others are providing. Only a fraction of what you all bring here is mentioned anywhere I have found. I pick up maybe 5-10% of this through Rantingly and a few other non-Pravda news feeds.
This is absolutely insane that (1) "journalists" are actively ignoring/trying to kill the story, and (2) if it truly is BS, that they are not lining up to support audits to shut up the deplorables.
This is absolutely insane that (1) "journalists" are actively ignoring/trying to kill the story, and (2) if it truly is BS, that they are not lining up to support audits to shut up the deplorables.
BREAKING: Maricopa County withholding subpoenaed hardware from election audit, citing alleged ‘security risk’ | Just The News https://t.co/dphKCkOhQS
— John Solomon (@jsolomonReports) May 6, 2021
Quote:
Bennett told Just the News that the state Senate's subpoena had requested "access or control of all routers and tabulators ... used in connection with the administration of the 2020 election" as well as "the public IP of the [routers]."
"I don't know why the routers in a tabulation and election center have anything to do with the Maricopa County Sheriff's Office or numerous federal agencies," Bennett said, noting that "the sheriff's department and the Maricopa County tabulation and election center aren't even in the same building."
Maricopa County spokesman Fields Moseley on Thursday afternoon said the county had "determined the information contained in Maricopa County's routers can be used as blueprints to intercept sensitive county data."
"Maricopa County has more than 50 different county departments, and the routers the Senate subpoena commanded the County produce support all of these departments, not just elections operations," Moseley said. "This includes critical law enforcement data that, by law, cannot be disclosed, as well as Maricopa County residents' protected health information and full social security numbers."
Good grief.Quote:
"By providing the routers, or even virtual images of routers, sensitive data and the lives of law enforcement personnel could be endangered," he added, stating that the routers "remain in the county's custody for the time being."
I don't see how that's possible. I can't imagine healthcare or SSN information being on a router at all. There isn't any place to store that kind of thing, nor would there be a reason to.
Hillary paid for warrant to spy on Trump.
Agree, this is stupid pushing that as a reason.FriscoKid said:
I don't see how that's possible. I can imagine healthcare or SSN information being on a router at all. There isn't any place to store that kind of thing, nor would there be a reason to.
I agree. And unless detailed logging was on somehow, there wouldn't be a record of where every packet on the network originated and terminated.FriscoKid said:
I don't see how that's possible. I can imagine healthcare or SSN information being on a router at all. There isn't any place to store that kind of thing, nor would there be a reason to.
Best guess of a blurry picture:
Patch panels
Switch with the patch cords from the building
Switch with the servers and router(?) plugged into it?
1U Server
1U Server
Router?
Bottom stuff - no idea. I guess bigger servers, looks like drive bays, but not sure they are on or in use.
I wish there was a clearer picture.
New Hampshire:
Okay. I am all for citizen involvement but I don't want that to devolve into an HOA meeting. Further, last I checked, Jovan was offering his services free of charge. Finally, on what authority can they obtain the ballots and machines to do so?
LinkQuote:
And all three of the members chosen were linked to the shady Verified Voting firm!
Now the people are fighting back!
A petition and fundraiser was formed at GiveSendGo for the Windham residents to hire computer expert Jovan Pulitzer to run an audit for the people.
** You can give to the fundraiser here:
From the the GiveSendGo account:
*We need to hire 2 auditors and legal representation. Your generous donations will not go to waste. We will make sure we continue this battle for FREE and FAIR elections for ALL!
If you love this state, country and your God given right to Liberty, please donate and share!
FOLLOW US ON FACEBOOK! www.facebook.com/nhvoterintegrity
Our group has done extensive research and would like to hire Jovan Pulitzer as our trusted forensic analyst. Our recourse is to hire him ourselves to conduct The Peoples' Audit!
The 'WINDHAM INCIDENT' is the largest unexplained voting discrepancy in NH state history and WE NEED ANSWERS!
WHAT HAPPENED?
The State Rep race had four open seats.
On Election Day, Nov. 3, 2020:
All four Republicans won
Winning Margin: 24 Votes (.005%)
Hand Recount Results on Nov. 12, 2020:
All four Republicans GAINED +300 Votes
Leading Democrat LOST (-99) Votes
With the help of many, including Senator Guida, we were able to pass a bill allowing for a forensic audit. The agreement is, Windham NH will select a forensic analyst, the NH Secretary of State and Attorney General will select a forensic analyst, and those two analysts will choose a third.
Right now, both the town of Windham and the NH SOS and AG have chosen a company that presents serious conflicts of interest. The choice for Windham is Mark Lindeman of Verified Voting, who is NOT a forensic Analyst. The people have spoken and have not been heard.
Okay. I am all for citizen involvement but I don't want that to devolve into an HOA meeting. Further, last I checked, Jovan was offering his services free of charge. Finally, on what authority can they obtain the ballots and machines to do so?
Rumble interview with Bennett HERE.
Quote:
Ken Bennett: You always wonder if a letter expressing concerns is a precursor to a lawsuit or something like that. We'll have to see if one turns into the other. I hope not.
Jordan: Do you any issues with the federal government interfering with the Arizona legislature-directed audit?
Ken Bennett: If they do interfere I see a big problem with that. If they want to send a letter to Senate President Karen Fann and ask her and me as a liaison to address a couple of questions, we'll do that. But if they do something more than that I think that would be interference.
Hobbs won't take questions.

FTR: Don't wear heels when your ass is that large. Nor pantsuits for that matter.
Read the rest HERE. Video at link.

FTR: Don't wear heels when your ass is that large. Nor pantsuits for that matter.
Read the rest HERE. Video at link.
Featured Stories
See All
19:50
23m ago
691
Keys to the Game: No. 8 Texas A&M vs. Georgia
by Luke Evangelist
12:39
2h ago
1.1k
Third base coach Will Fox is growing comfortable in new on-field role
by Ryan Brauninger
Recruiting industry's evaluation process is evolving in information era
by Ryan Brauninger
Zachary Klement
***Official 2024 - 2025 Dallas Mavericks Season Thread***
in NBA & Other Basketball
13
DannyDuberstein
***Official 2024 - 2025 Dallas Mavericks Season Thread***
in NBA & Other Basketball
11